4 Reasons to Assess Risks in Your Databases - DEEP
Today, we see daily reports in the press about hacking, data breaches, and massive service outages. At the same time, data is more central than ever to strategic development and the sustainability of organizations. However, this data is stored in databases, which are themselves within complex IT infrastructures.
Here are four reasons to evaluate the security measures in place and conduct an IT risk analysis, and why you should focus on your databases. Data security is paramount for businesses, regardless of their size.
What is IT risk analysis?
IT risk analysis is one of the steps in risk management, which is defined by the ISO 31000 standard as the set of "coordinated activities to direct and control an organization with regard to risk."
In general, there are three main objectives of IT risk management:
- Evaluate the measures in place according to your security criteria (Availability, Integrity, and Confidentiality, in particular)
- Improve the security of the information system (IS)
- Prove and test the reliability of the IS
Risk is generally defined by the "risk equation," which is:
RISK = THREAT x VULNERABILITY x IMPACT
In this equation, a threat corresponds to the origin of the risk, its source, the potential attack that could harm the assets. Vulnerability is a security flaw at the level of an asset. Finally, impact can be defined as a level of severity.
To reduce risks and protect assets, organizations must define a risk management policy, which in turn leads to the implementation of a security action plan for assets, particularly data. This action plan must also take into account the likelihood and acceptance of risks by the organization.
Now that we have reviewed the fundamentals together, here are 4 reasons to conduct a risk analysis of your information system, particularly your databases.
Reason No. 1: Your data is critical, and businesses of all sizes are concerned
Do you still know many companies that operate solely with paper files?
Today, all companies manage digital data. This data is their raw gold, and many companies have understood this by injecting it into Big Data, Machine Learning, or Data Analytics tools to exploit it to the maximum and create more value.
Moreover, today, an organization can no longer function without access to its information system because it contains critical applications (order processing solutions, logistics, CRM, HR, Accounting, Patient Records...) but most importantly, essential data for the organization's activities.
It is therefore crucial for these organizations to protect their information system and especially their data.
In 2018, according to an Insee study published in April 2020, 16% of companies with more than 10 employees reported experiencing an IT security incident (unavailability, destruction or alteration of data, disclosure of confidential data, etc.). More specifically, 13% of small companies (10 to 19 employees) encountered security incidents compared to 30% of large companies (more than 250 employees).
The good news is that 87% of companies with more than 10 employees have taken measures regarding the security of their information systems, such as training, security tests, etc.
This report also tells us that 67% of companies outsource all or part of their IT security activities.
Reason No. 2: It is a fact: databases are prime targets
By definition, the DBMS (Database Management System) is independent of applications. Thus, it is possible to access data without going through the application or its controls.
According to the 2019 Data Breach Investigations Report by Verizon, database servers are among the top 5 assets affected by data breaches, alongside email servers, application servers, and workstations.
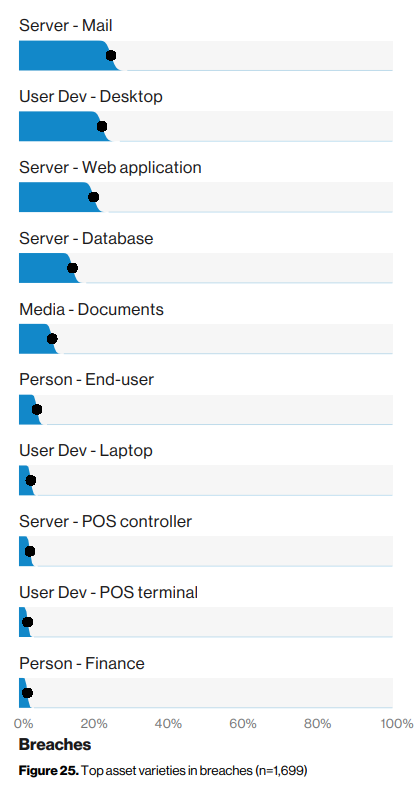
36% of data breaches are due to poor database configuration, both on-premise and in the cloud. The report also tells us that 34% of attacks involve internal actors. These are at least two important factors to consider. Hence, the necessity for your organization to identify the measures implemented within your information system and evaluate the associated risks, to then address or accept them with full knowledge of the facts.
Reason No. 3: New uses (Business, Cloud...) create new security vulnerabilities
The various business functions within organizations are evolving with digital transformation and the economy. Thus, new uses are emerging:
- Business functions need to open access to data to increase the value generated by the organization;
- Partners and/or B2B or B2C clients may sometimes access the organization's information system to optimize costs and timelines;
- IT teams, in particular, need to multiply data copies to perform backups, disaster recovery (DR/BCP), or tests to facilitate the development of new applications...
Overall, these changes in usage make the information system (IS) more complex:
- Multiplication of databases and their locations (Cloud, SaaS, Shadow IT...);
- Interfacing between applications, organizations, mobile applications...;
- Connection with numerous applications, each with their own specificities.
From an information security perspective, this reinforces the necessity to identify vulnerabilities, the security measures implemented, and ultimately to evaluate the security risks specific to your organization's IS.
Reason No. 4: You must comply with regulations
Regulations, certifications, and standards at the national, European (GDPR, NIS, etc.), international (ISO 27001, etc.), or sectoral (HDS, PCI-DSS, etc.) levels are evolving to address cybersecurity issues and protect individuals. All now incorporate the principle of risk assessment.
Being compliant with rules and standards is important for several reasons:
- To protect and maintain your activity by aligning with standard recommendations to safeguard your information system;
- To protect your assets and provide guarantees of quality, trust, and security to your regulatory authorities, clients, and partners;
- To ensure that your partners adopt an appropriate level of security and continuity of service.
To be stronger, you need to know your weaknesses... Do you know your IT security vulnerabilities?
If you want to learn more about IT risk analysis and how to implement risk management, access the replay of our webinar "How to successfully analyze and manage the risks of your Oracle databases?".
Also discover our Cyber Resilience offering.
Contact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Data & AI
Connected objects, new sources of usable intelligence
Connected objects are proliferating in all sectors. The challenge now is to make effective use of the data they generate. Thanks to an integrated approach combining connectivity, the cloud, artificial intelligence and security, DEEP can help organisations to set up ecosystems that make the most of data, transforming IoT and M2M into powerful levers of efficiency.
Published on
21 July 2025
Key Challenges in Successful Digital Transformation for Public Sector
Explore the key challenges and success factors of digital transformation for local authorities: budgets, skills, cybersecurity, inclusion, data sovereignty and sustainability.
Published on
13 May 2025
Federated Governance: A Key Pillar for Successful Data Mesh Implementation
Learn why federated governance is a critical organizational pillar in a Data Mesh architecture. A strategic issue for data-driven companies.
Published on
12 December 2023