Landing Zone Cloud security: Protecting your resources - DEEP
According to Gartner, by 2025, the root cause of more than 99% of cloud computing breaches will be misconfiguration or end-user errors*.
In our previous article on best practice for network design and management within a Cloud Landing Zone, we highlighted the fundamental importance of a robust and secure network infrastructure as a cornerstone of a successful transition to the Cloud. However, securing a Cloud Landing Zone is not limited to the network framework.
By placing security at the heart of Cloud governance, we will explore how CIOs can take advantage of the full potential of the Cloud, while maintaining a robust security posture (Zero Trust Approach).
Fundamentals of Landing Zone Security
Landing Zone security involves putting in place controls, policies and solutions designed to protect resources, data and managed services. Landing Zone security, which is the starting point for cloud adoption, needs to be thought through and integrated from day one. Key security concepts to consider include:
- Data security: Ensuring that data stored and processed in the cloud is protected against unauthorised access, leakage and loss.
- Access Control: Defining who can access which resources in the cloud and with what rights, using mechanisms such as multi-factor authentication and role-based access control (RBAC).
- Network Security: Protecting the network against intrusions and attacks by segmenting traffic, encrypting data in transit and deploying firewalls.
- Identity Management: Securely identify, authenticate and authorise users and services, ensuring rigorous management of credentials and access.
- Compliance: Complying with industry and government regulations
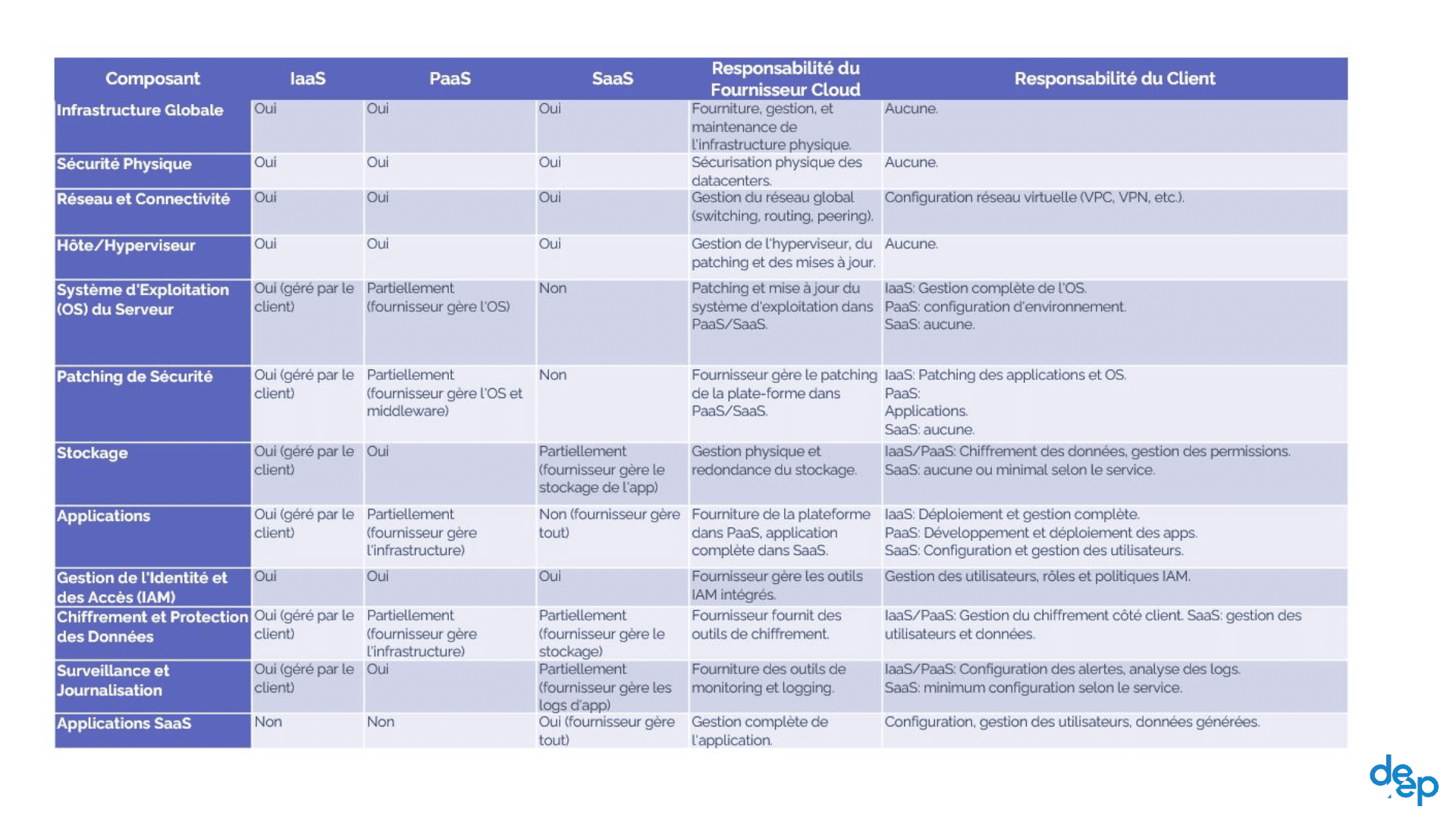
Shared Responsibility Model
In the cloud, security is often managed on a shared responsibility model between the cloud service provider and the customer. It is vital to have a clear understanding of which aspects of security the Cloud Service Provider (CSP) covers and which are your responsibility.
The service model determines the level of responsibility:
-
IaaS (Infrastructure as a Service): The customer mainly manages the virtual machines, storage, networks and operating system. The cloud provider manages the physical infrastructure, network and virtualisation.
-
PaaS (Platform as a Service): The cloud provider manages more aspects than in IaaS, including the operating system, databases and other middleware. The customer focuses primarily on developing and managing the applications deployed on the platform.
-
SaaS (Software as a Service): The cloud provider manages almost everything, including the application itself. The customer simply uses the application via the cloud, concentrating on managing the users and the data generated by the application.
The Zero Trust Approach to Landing Zone Architecture
The Zero Trust approach is establishing itself as a new paradigm, asserting that no person, system or service, whether internal or external, should be considered secure a priori. In a Cloud Landing Zone, this systematic mistrust means that every attempt to access resources in the Landing Zone must be carefully checked and validated.
Micro-segmentation to isolate resources
Micro-segmentation is a key technique in the Zero Trust approach, dividing the network into smaller, more manageable and more secure segments. This reduces the attack surface and limits the ability of malicious actors to move throughout the network. Each micro-segment has its own defined access controls, ensuring that applications and services are isolated from each other.
Active monitoring
Complete visibility of activity within the Landing Zone is essential. Monitoring and analysis tools continuously collect and examine traffic data and security events to detect and respond to suspicious activity.
Dynamic and adaptive policies
Security policies in a Zero Trust architecture must not remain static. They must adapt to changing contexts and levels of risk. Access is constantly reassessed, and rights can be modified or revoked as a function of changes in user behaviour or status.
Minimisation of privileges
The application of the principle of least privilege is even more critical in the Zero Trust approach. Access is limited to what is strictly necessary to complete a task, which minimises the risks in the event of credentials being compromised or access policies being violated.
Identity and Access Management
Identity and Access Management (IAM) is at the heart of security in cloud environments. It defines how users are identified and authenticated, and what permissions they are granted on IT resources. By carefully controlling who can access what, IAM plays a crucial role in protecting against unauthorised access and data leakage.
To effectively implement IAM in a cloud environment, we recommend that you adopt the following practices:
Identity Federation
Identity federation enables users to authenticate to cloud consoles and applications using their Active Directory credentials. This means they only need one set of passwords to access all resources, simplifying access management and improving their experience. As well as making authentication smoother, this approach maintains a high level of security. Protocols such as SAML and OpenID Connect are used to ensure this integration between Active Directory and cloud services.
Multi-Factor Authentication (MFA)
MFA requires users to provide two or more proofs of identity to access resources, adding an extra layer of security. By combining something the user knows (such as a password) with something they have (such as a smartphone or token), MFA significantly reduces the risk of unauthorised access.
Access Monitoring and Review
Continuous monitoring and regular review of access is essential to detect and correct inappropriate or obsolete permissions. Identity and access management tools can automate these reviews, making it easier to detect anomalies and ensure compliance with security policies.
Data protection
While identity management locks down access to resources, data protection focuses on the security of the data itself, both at rest and in transit. This chapter covers the essential technologies and practices for ensuring the confidentiality and integrity of data in the cloud.
Data encryption
Encryption is the cornerstone of data protection. Encrypting data ensures that data stored on disks or cloud services is inaccessible without the decryption key. Similarly, encryption in transit protects data exchanged between services and users, preventing malicious interception.
Encryption key management
Secure management of encryption keys is essential to guarantee the effectiveness of encryption.
Every Cloud Provider offers to encrypt the desired resources for you with their keys. However, depending on regulatory constraints, they will also provide you with a Key Management Service (KMS). It offers features for creating, storing and managing your encryption keys securely, while guaranteeing their availability for encryption and decryption operations.
Data backup and recovery
Implementing backup and recovery strategies is crucial to data resilience. Best practice includes regular backup of critical data, replication of data for resilience against regional and availability zone failures, and regular testing of recovery procedures to ensure effectiveness in the event of a disaster.
Compliance and Data Protection Regulations
Compliance with local and international data protection regulations (such as the GDPR) is not only a legal obligation but also a key element of customer confidence. Particular attention must be paid to data localisation, access rights, and data breach management processes.
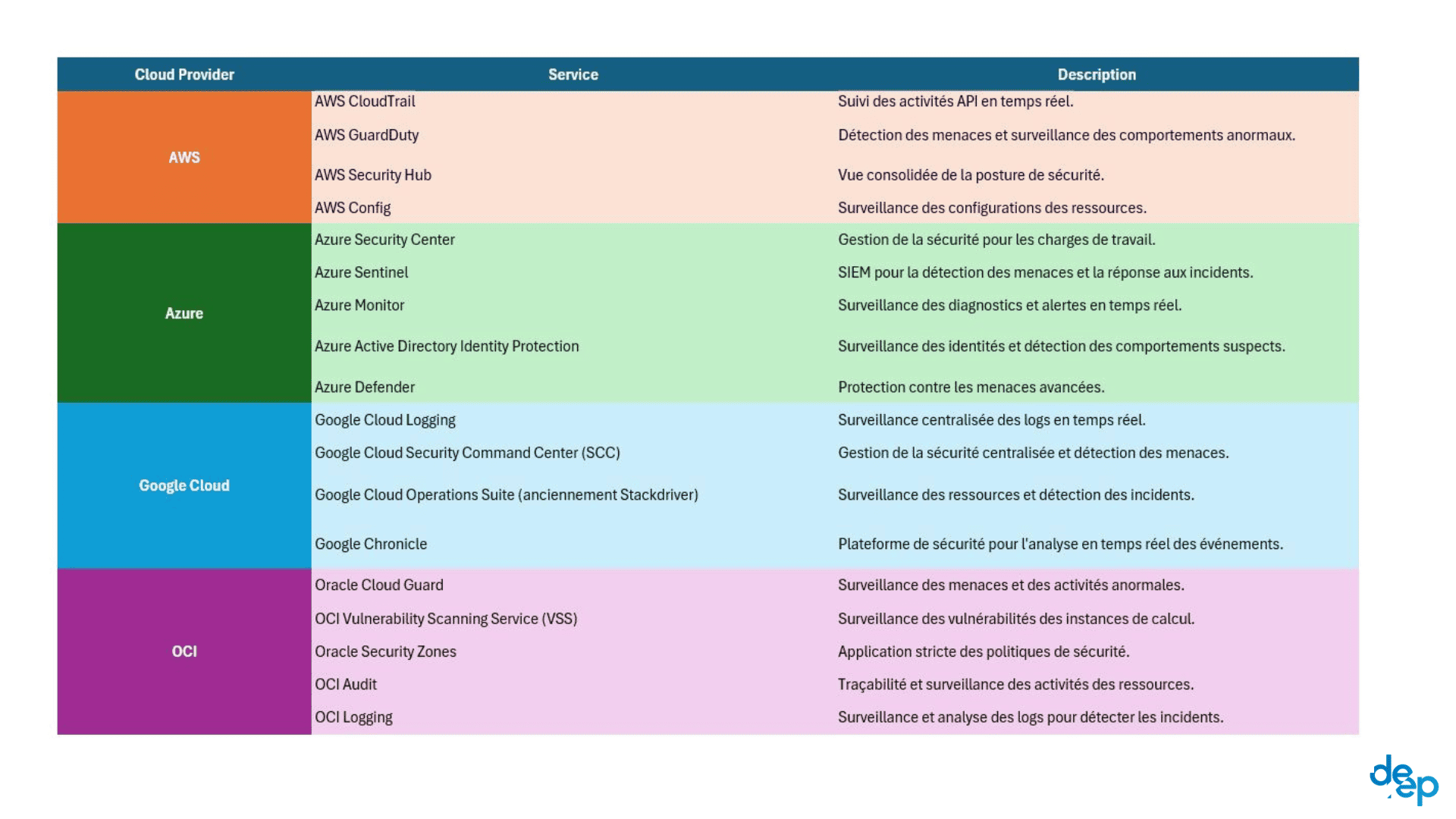
Real-time monitoring
The adoption of centralised monitoring systems is essential for security. These systems continuously scan the logs, metrics and security events of all cloud resources, providing a comprehensive, real-time analysis of potential security breaches.
For each cloud provider, here are the specific services that provide this real-time monitoring:
Automated Alerts
These alerts should be configured to signal critical incidents that require immediate attention, ensuring that corrective measures can be taken without delay.
In conclusion, the security of a Cloud Landing Zone is a key issue for any company wishing to migrate to the Cloud. By adopting a global and proactive approach, incorporating fundamental principles such as Zero Trust and putting in place rigorous control mechanisms, it is possible to build a secure and reliable cloud environment.
As experts in digital transformation, DEEP can help you design and implement your Landing Zone Cloud. Our teams will help you define a security strategy tailored to your specific needs, implement best practices and ensure continuous monitoring of your environment.
Contact our Cloud experts today to assess the best solution for your cloud project!
* Source : https://www.gartner.com/smarterwithgartner/is-the-cloud-secure
Contact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Cloud
Work Smarter with Microsoft 365 and Teams
Stop sending files by email! Discover how Microsoft 365 and Teams help SMEs collaborate efficiently, share securely, and boost productivity.
Published on
04 November 2025
The Cloud, more than ever the foundation of digital transformation
Digital transformation is accelerating in Luxembourg, driven by the cloud. With the upcoming arrival of Azure Extended Zone in Luxembourg, organisations have new opportunities to combine agility and compliance.
Published on
17 October 2025
DORA: guaranteeing an effective Exit Strategy
To help cloud-based financial services providers comply with DORA and support their operational resilience, Deloitte and DEEP are implementing an innovative ‘Exit Strategy’ solution.
Published on
20 December 2024
Got a project? Questions?
Send us a message and our experts will get back to you quickly.
DEEP? Your digital ally!
With DEEP, turn your IT projects into measurable and sustainable growth drivers.





